 Update: With the help of security researchers, Apple over the weekend quickly blocked a cyberattack aimed at infecting Mac users with file-encrypting malware known as ransomware.
Update: With the help of security researchers, Apple over the weekend quickly blocked a cyberattack aimed at infecting Mac users with file-encrypting malware known as ransomware.
Facebook, Twitter, and the headlines on all the computer new sites this morning are counting the first occurrence of Mac ransomware found in an application distributed to users computers. In fact, I’ve already had emails from people I provide support for worried that they may be infected. Here are a couple of things that are important to understand about Malware such as this.
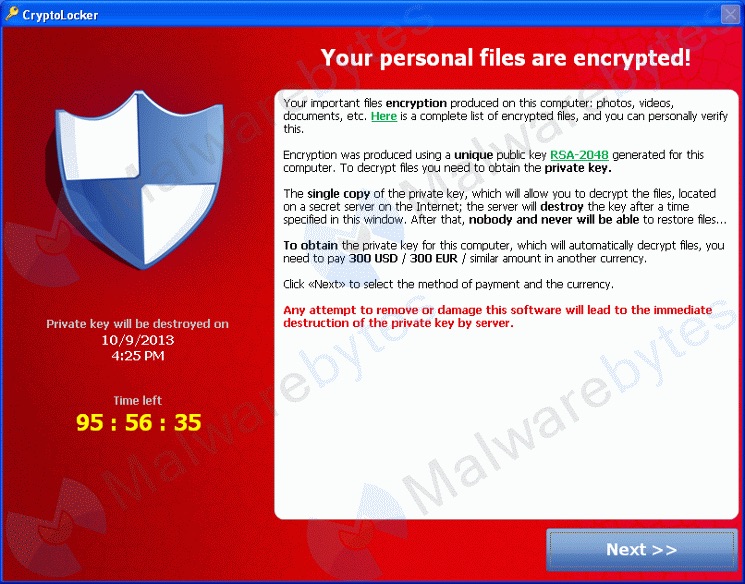
Here is the description of the malware that was found from Appleinsider’s website:
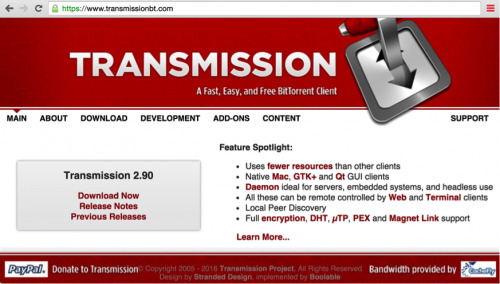
“Users who downloaded the Transmission BitTorrent client on Friday or Saturday are being warned to update to the latest 2.92 version to avoid being targeted by a ransomware that infiltrated an earlier version of the open source software…… The malware then “demands that victims pay one bitcoin (about $400) to a specific address to retrieve their files.” Researchers say the malicious code is “under active development” and seems to be trying to also encrypt users’ Time Machine backups to also prevent them from being able to recover their backed up data.”
So basically, unless you downloaded the transmission bit torrent client recently, you have nothing to worry about this particular instance.
Some of you may ask what is a bit torrent client? Wikipedia says, “BitTorrent is a communications protocol for the practice of peer-to-peer file sharing that is used to distribute large amounts of data over the Internet. BitTorrent is one of the most common protocols for transferring large files, and peer-to-peer networks have been estimated to collectively account for approximately 43% to 70% of all Internet traffic”
Basically, bit torent clients are used to download large files, typically large files such as pirated movies, still in applications, and other things that you can’t make generally available on the Internet.
So again, unless you’re downloading files of this type using this particular software you don’t need to worry about this particular infection.
The big concern about this particular malware is that it’s only the beginning of others that we may see. Only time will tell, but I fully expect to see more of these in the near future. These types of infections are very prevalent on the Windows side and I have seen a number of computer users lose all their data as a result.
So what’s a person to do?
Back up your data. Not just once, but twice, and keep one copy of the back up not connected to your computer. I typically back up with time machine is my every day back up and then use carbon copy cloner as a secondary back up on a drive it is not mounted to my computer. This way if I were to get infected with something like this, and it were to infect my back up that’s connected, I still have an additional copy of my data to recover from.
People think that’s a little paranoid, but believe me if you ever need to recover files having a second copy certainly makes you feel better. With external hard drive’s running about $60, there’s really no excuse, get a second Drive, purchase Carbon Copy Cloner, and set up a back up routine for yourself. If there are any problems in the future, you’ll be happy you did.